I just received my WiiM Pro and love it so far.
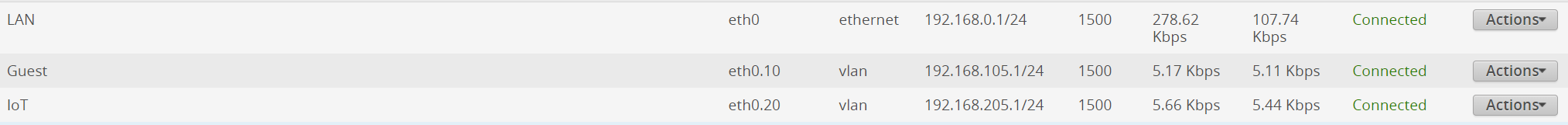
The only thing I'd like to figure out is how to use it on my "segregated IoT network" (vlan). I don't trust IoT devices on my main network, so I created a separate network in my AsusWRT Merlin RT68U, and the traffic between those devices and the main network is managed by iptables rules. So far, all the devices on the IoT network can only access the internet, but cannot be reached by devices from the main network, or reach devices in the main network.
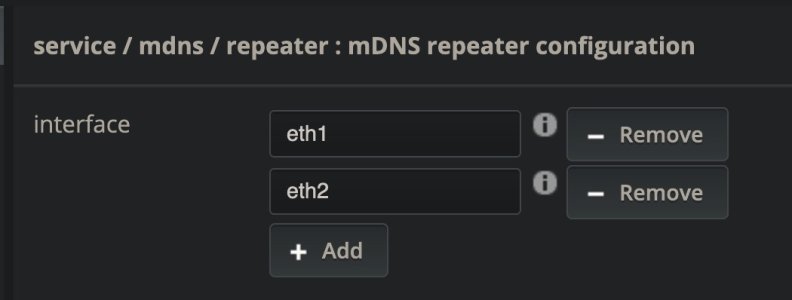
I set up the WiiM with a fixed IP (which has downsides, but manageable) and I enabled the mDNS redirector using the built-in Avahi, which runs by default
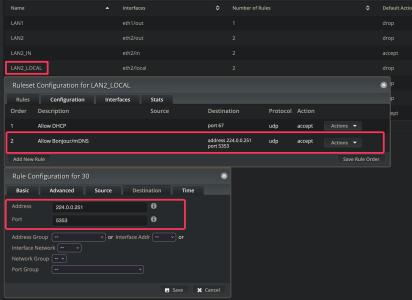
Do you have the equivalent of the above rules for iptables? The Merlin firmware is basically a Linux machine that allows to do things that are not doable with the GUI. I'm not sure how I can enable "mDNS multicast on 5353" using iptables
EDIT: I'm having problems with the Avahi configuration, but I think I got the iptables part. My vlan is on br1 and the WiiM address is 192.168.20.170. I think I need the below
Code:
# allow devices on main LAN to access WiiM on IoT vlan
iptables -I FORWARD -i br0 -o br1 -d 192.168.20.170 -j ACCEPT
With this, the great WiiM Watcher Chrome extension works perfectly (I think it was developed by
@onlyoneme, thanks so much for that!)
Then a subset of the below
Code:
# allow mDNS traffic between networks
iptables -I INPUT -i br1 -p udp -m multiport --dport 5353 -j ACCEPT
iptables -I FORWARD -i br1 -p udp -m multiport --dport 5353 -j ACCEPT
iptables -I INPUT -i br1 -p tcp -m multiport --dport 5353 -j ACCEPT
iptables -I FORWARD -i br1 -p tcp -m multiport --dport 5353 -j ACCEPT